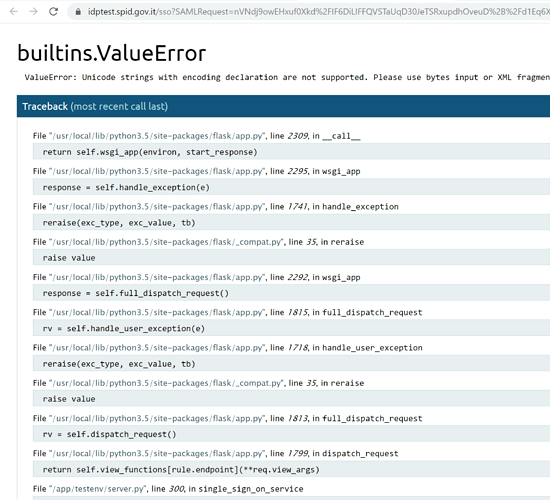
Buongiorno, lo spid-testenv2 mi da errore di decodifica della AuthnRequest SAML
Nota: le chiavi qui riportate sono usate solo in sviluppo, quindi le condivido senza problemi.
Errore da SPID-TESTENV2:
Impossibile decodificare l’elemento ‘SAMLRequest’
Il service provider tenta l’autenticazione SPID producendo una pagina HTML autopostante come indicato nelle regole tecniche per SPID.
SAML REQUEST CODIFICATA PRESENTE NELLA POST
(utilizzando la libreria https://github.com/italia/spid-spring alla quale e’ stato aggiunto l’identity provider {
“identifier”: “Testenv2”,
“entityId”: “http://localhost:8088”,
“name”: “Testenv2”,
“imageUrl”: “https://www.spid.gov.it/assets/img/richiedi-spid/logo-poste.svg”
}):
pVdZk6LMEn03wv9gMI%2BGTYG7MfYXhbhgKwiC28uNAopF2aRA0F9%2FcWmje76euR1z36oyszKTPIfi8POf3PcqJxwTNwz6FPMCqAoOjNB0A7tPaeqo1qH%2Bef1JkO9FPZgmTqDgY4pJUinOBaR3c%2FSpNA56ISIu6QXIx6SXGL0lnM967AvoRXGYhEboURVICI6TotAgDEjq43iJ45NrYCEwcd6nwO8jNGXWp5wkiUiPpknkmi8eNgz84ia3XY1EcdFwLS4aowkOzOsqKlLgImWSxK6eJviesgj7XJWhKnxxzA1QchvBtUpRxAsN5DkhSXod0OnQhIRUReD71H%2BQbpodE9TqbYBrDavdqulsh6l1MNZ1tt2yELaKSLJAhLgn3Kcs5F3bEAhJi5IkQUHSp1jAdGugWWPrKgN6DbbHdl9aXWZHVRaPaXFucMfgT6PV70GkN1HVRW0hLVWqsnrHsgig7sixvVv1%2BANm7J8To3ccqMoojH2U%2FDn8ailQsG6hvSRGAXFxkFAVsXDIKfJcy8XxbxCkXr80%2F6Q%2Ftv760yS9pWsXKKUxfjyISZ5wZVn2ktVfwtimWQAADbp0EWMS1%2F5BPc9iUwis8LYdoCAM3AJi93LDfY4TJzQr0LPD2E0c%2FzeJGZoB18Q1nBs1g2kEPyj6c2vfTgQa7x3W%2FDDGP2KCasRBbLP1SKlgC8fFu4grmiL0qR%2FfYt7tpHoF4AoG%2Bbz9n119mhsOTtgLI1y8Xe8P9%2Bjs%2Bwm%2Fnhf97x551y5ewm8O71ObxcyYR1%2F3JCvkpfhR5TnD%2B%2FYXEjxBez9S2N7w%2Bekv1jfPHY4l%2FLSfh2bqpeQ1OCs7rKx3adytVi23Xq9K%2FikbiKsDP87Olxi6xxkm6TmS4oXmd4cGe7AP0tS2QqXhH1tslHpOfYGHztJG5dLR9GiSp2%2FQESV9Oteh1alW5X11Jq2muWErre2Jb68P80GKkdydNvEbPyWT8zAbL2dRao155rI3crhTTbQvl5rDk3AWRXBJF3lrKR50gHVndUGp21FbqxDmyVIbkVYTHtxJVVtrwTRrCwrnrazJcTXKps7EmTO%2BhazNMiuXBok7vrSFhhdsmLUdtcJsJG1kxY2VHYcb8YZw2TTuANduJKoHYWyMAh6uYIeY612ob5B4Arm9SxvCSRHLpSo9dt3NCMRMXc23DEEkM3VzO7lw%2ByH2Uul0YI%2F1rN%2B%2FAfc%2B7Ovgh3lxsxe3yyuUIXfzPi13zD8CRf8K46YJujxK0HMzuF50VnEVJPh1Lgg8vAwGEKc2zAQO2sIUioc1iWbqJCSdOQTjwfI4Xgp6nZeHHCdrcM7Z%2BWgPNc4WVxycz%2FmNmKG1nJZL%2Bni137JaijZyNnEMca4a%2BZyH9bmqgflFy9dX2%2F5mY562PdzOlW02glt%2BJct84boYY%2B9QLs383NuyojfzPVD0yQl7KHL24egc3HE3AxyUhyMIpQGUO%2FDqH9hvxXoIv%2BJnufS3DP2KnwWWf8nQr%2FhZLv0tQ7%2FiZ7n0twz9ip8Fpv9iaMGYgochAzN1D80rCyZyYziyZc08W4TJUt0%2FRD45N8LLqamPO3q74dvZJNvy5dJKAXuOs7NRCP8YzV%2FZoACVg1oGsyFHX37FXhuVS3f0C8R3b6jB1fdNxfbSlYJaw9msudAXq4t%2FBLE180HQbu3dHYCYkBPnbhv0ZOw7B1OJ2ZEp%2BLSCuuVSppC1PASGE3Z3e2VVd1AzCI1g6R%2Fkpjq5iEG1oyGLF6saOkW7DtqCI6dJPD8%2FMNFgVkfM7Nxsxeuht5TUcim0gdRMzgM4PA4Jx85G5zdpNpa508bPnGQgHTeWF1%2B4%2BnmaTpxgEjej%2BQKIm86ZSxR0Tq32nmYnDRGe3fhULqHAloxm3t4ZW9gVLuqwmtDAOE3eJrqP90Q7MsxZGAR8d7vERymcAsteiKwEOHV8Pqr%2Bm0%2BDFQjVRML1vFziB7x0drbytgH0%2BmIjNGE0XJ9sVqHl42zbVuTWDqExqTuLQdaCjxvp16vjabxfLvTHTwn98VvzkGRR76qNBH4Req5x%2FqjMvi2n%2Fx9lRj%2FbeOh5bN7UfSGSE5wnf9XPIPQjFLvkKj5xjozkIT97HzMPvEJbFp%2FlDxW%2BK0WfOvGqBm5a0Q5P11%2BAZbGesXfB%2BGWx14eY%2FM3TPtyff3Be%2Fws%3D
NOTA: la codifica in BASE64 avviene nella classe SPIDIntegrationUtil del progetto spid-spring-integration nel metodo seguente :
public String encodeAndPrintAuthnRequest(AuthnRequest authnRequest) throws IntegrationServiceException {
String requestMessage = printAuthnRequest(authnRequest);
Deflater deflater = new Deflater(Deflater.DEFLATED, true);
ByteArrayOutputStream byteArrayOutputStream = null;
DeflaterOutputStream deflaterOutputStream = null;
String encodedRequestMessage;
try {
byteArrayOutputStream = new ByteArrayOutputStream();
deflaterOutputStream = new DeflaterOutputStream(byteArrayOutputStream, deflater);
deflaterOutputStream.write(requestMessage.getBytes()); // compressing
deflaterOutputStream.close();
encodedRequestMessage = Base64.encodeBytes(byteArrayOutputStream.toByteArray(), Base64.DONT_BREAK_LINES);
encodedRequestMessage = URLEncoder.encode(encodedRequestMessage, "UTF-8").trim(); // encoding string
}
catch (UnsupportedEncodingException e) {
log.error("encodeAndPrintAuthnRequest :: " + e.getMessage(), e);
throw new IntegrationServiceException(e);
}
catch (IOException e) {
log.error("encodeAndPrintAuthnRequest :: " + e.getMessage(), e);
throw new IntegrationServiceException(e);
}
return encodedRequestMessage;
}
SAML REQUEST PRIMA DELLA CODIFICA:
```xml
<?xml version="1.0" encoding="UTF-8"?>
<samlp:AuthnRequest xmlns:samlp="urn:oasis:names:tc:SAML:2.0:protocol" AssertionConsumerServiceIndex="1" AttributeConsumingServiceIndex="1" Destination="http://localhost:8088/sso" ID="_abdd8d0-370e-4f76-b281-8eebb276faef" IsPassive="false" IssueInstant="2019-05-28T08:57:47.234Z" ProtocolBinding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Version="2.0">
<saml2:Issuer xmlns:saml2="urn:oasis:names:tc:SAML:2.0:assertion" Format="urn:oasis:names:tc:SAML:2.0:nameid-format:transient" NameQualifier="https://www.HIDDEN.it">https://www.HIDDEN.it</saml2:Issuer>
<ds:Signature xmlns:ds="http://www.w3.org/2000/09/xmldsig#">
<ds:SignedInfo>
<ds:CanonicalizationMethod Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#" />
<ds:SignatureMethod Algorithm="http://www.w3.org/2001/04/xmldsig-more#rsa-sha256" />
<ds:Reference URI="#_abdd8d0-370e-4f76-b281-8eebb276faef">
<ds:Transforms>
<ds:Transform Algorithm="http://www.w3.org/2000/09/xmldsig#enveloped-signature" />
<ds:Transform Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#" />
</ds:Transforms>
<ds:DigestMethod Algorithm="http://www.w3.org/2000/09/xmldsig#sha1" />
<ds:DigestValue />
</ds:Reference>
</ds:SignedInfo>
<ds:SignatureValue />
<ds:KeyInfo>
<ds:KeyValue>
<ds:RSAKeyValue>
<ds:Modulus>nyRZeRWZur9++fi33+OmvwCNVkDGwyzrAiqLesuypOrPUm9Ec2kgkOJgfoR4mq62pulh3PeEhSga
qdl/sxuKAhNObJMbAf8++Qj+LOVJxcgR6YvD7WkMCueaQ9J5eKDJsHyEwGSLpufGD1zjcxAZTdaj
5EvIyNN0zuPx6SNkb0ebhVzaui8T6VoAxtSUFs65AkiH+UWUnJw7IRBlVfHqVFwJhHhM1mfafXSw
CtiGz7I4lnX1Wgp6owFOXQRirRZBe4rXsBwJr80ig4tTlAArcFnDAVA8sdWZobXaNv0xgZu4IvRN
+/GiiXF0r13TxY1saswdbdYHzBjEeluOvk2q3w==</ds:Modulus>
<ds:Exponent>AQAB</ds:Exponent>
</ds:RSAKeyValue>
</ds:KeyValue>
<ds:X509Data>
<ds:X509Certificate>MIIDAzCCAeugAwIBAgIJANkWspLTHos8MA0GCSqGSIb3DQEBBQUAMBgxFjAUBgNVBAMMDXNwaWQu
bGVjY2UuaXQwHhcNMTcxMDA3MTU0MzUxWhcNMjcxMDA1MTU0MzUxWjAYMRYwFAYDVQQDDA1zcGlk
LmxlY2NlLml0MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAnyRZeRWZur9++fi33+Om
vwCNVkDGwyzrAiqLesuypOrPUm9Ec2kgkOJgfoR4mq62pulh3PeEhSgaqdl/sxuKAhNObJMbAf8+
+Qj+LOVJxcgR6YvD7WkMCueaQ9J5eKDJsHyEwGSLpufGD1zjcxAZTdaj5EvIyNN0zuPx6SNkb0eb
hVzaui8T6VoAxtSUFs65AkiH+UWUnJw7IRBlVfHqVFwJhHhM1mfafXSwCtiGz7I4lnX1Wgp6owFO
XQRirRZBe4rXsBwJr80ig4tTlAArcFnDAVA8sdWZobXaNv0xgZu4IvRN+/GiiXF0r13TxY1saswd
bdYHzBjEeluOvk2q3wIDAQABo1AwTjAdBgNVHQ4EFgQUdyfs1wubmkpmsy4ozv5bG8b74mgwHwYD
VR0jBBgwFoAUdyfs1wubmkpmsy4ozv5bG8b74mgwDAYDVR0TBAUwAwEB/zANBgkqhkiG9w0BAQUF
AAOCAQEAnZKa4B3j5RgluVRa6ELL5PbPVzmq0rfLm0n76jiZ0AessvBiY4/HGmhkdRr2FdIm/Ra9
wRsWQE0cho9ZjRV3ha5nocnSmkQ5THzNn+8UafDN+UavpZ8aY0qBUODDMk1pCL3a1Ly56rWElSOT
og0O5tyCAEqEsB2LFyKOLGQBvXmwhtCOqXflrzB3yJuHhnHr5pMP0NX8yBtRayuf7j/2H4NAyirv
angOc5x7ZcYA9IzTE+t/0cvHKHbmejsUq11yICnD9YSeqOoJ0fgPN2O0BTGyqTmKm/0V0oTtOe3x
DCDOyhYQY40b3PXI5ApEWvg2R/QqLY7RQ6ZaaGs3hPCw6A==</ds:X509Certificate>
</ds:X509Data>
</ds:KeyInfo>
</ds:Signature>
<saml2p:NameIDPolicy xmlns:saml2p="urn:oasis:names:tc:SAML:2.0:protocol" Format="urn:oasis:names:tc:SAML:2.0:nameid-format:transient" />
<saml2p:RequestedAuthnContext xmlns:saml2p="urn:oasis:names:tc:SAML:2.0:protocol" Comparison="exact">
<saml:AuthnContextClassRef xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion">https://www.spid.gov.it/SpidL2</saml:AuthnContextClassRef>
</saml2p:RequestedAuthnContext>
</samlp:AuthnRequest>
Metadata Service Provider (installato nel testenv2):
```xml
<?xml version="1.0"?>
<md:EntityDescriptor
xmlns:md="urn:oasis:names:tc:SAML:2.0:metadata"
xmlns:ds="http://www.w3.org/2000/09/xmldsig#"
entityID="https://www.HIDDEN.it"
ID="_397e220-3ce8-4374-b35d-003c5ab1a64a">
<md:SPSSODescriptor
protocolSupportEnumeration="urn:oasis:names:tc:SAML:2.0:protocol"
AuthnRequestsSigned="true"
WantAssertionsSigned="true">
<md:KeyDescriptor use="signing">
<ds:KeyInfo xmlns:ds="http://www.w3.org/2000/09/xmldsig#">
<ds:X509Data>
<ds:X509Certificate>MIIDAzCCAeugAwIBAgIJANkWspLTHos8MA0GCSqGSIb3DQEBBQUAMBgxFjAUBgNV
BAMMDXNwaWQubGVjY2UuaXQwHhcNMTcxMDA3MTU0MzUxWhcNMjcxMDA1MTU0MzUx
WjAYMRYwFAYDVQQDDA1zcGlkLmxlY2NlLml0MIIBIjANBgkqhkiG9w0BAQEFAAOC
AQ8AMIIBCgKCAQEAnyRZeRWZur9++fi33+OmvwCNVkDGwyzrAiqLesuypOrPUm9E
c2kgkOJgfoR4mq62pulh3PeEhSgaqdl/sxuKAhNObJMbAf8++Qj+LOVJxcgR6YvD
7WkMCueaQ9J5eKDJsHyEwGSLpufGD1zjcxAZTdaj5EvIyNN0zuPx6SNkb0ebhVza
ui8T6VoAxtSUFs65AkiH+UWUnJw7IRBlVfHqVFwJhHhM1mfafXSwCtiGz7I4lnX1
Wgp6owFOXQRirRZBe4rXsBwJr80ig4tTlAArcFnDAVA8sdWZobXaNv0xgZu4IvRN
+/GiiXF0r13TxY1saswdbdYHzBjEeluOvk2q3wIDAQABo1AwTjAdBgNVHQ4EFgQU
dyfs1wubmkpmsy4ozv5bG8b74mgwHwYDVR0jBBgwFoAUdyfs1wubmkpmsy4ozv5b
G8b74mgwDAYDVR0TBAUwAwEB/zANBgkqhkiG9w0BAQUFAAOCAQEAnZKa4B3j5Rgl
uVRa6ELL5PbPVzmq0rfLm0n76jiZ0AessvBiY4/HGmhkdRr2FdIm/Ra9wRsWQE0c
ho9ZjRV3ha5nocnSmkQ5THzNn+8UafDN+UavpZ8aY0qBUODDMk1pCL3a1Ly56rWE
lSOTog0O5tyCAEqEsB2LFyKOLGQBvXmwhtCOqXflrzB3yJuHhnHr5pMP0NX8yBtR
ayuf7j/2H4NAyirvangOc5x7ZcYA9IzTE+t/0cvHKHbmejsUq11yICnD9YSeqOoJ
0fgPN2O0BTGyqTmKm/0V0oTtOe3xDCDOyhYQY40b3PXI5ApEWvg2R/QqLY7RQ6Za
aGs3hPCw6A==</ds:X509Certificate>
</ds:X509Data>
</ds:KeyInfo>
</md:KeyDescriptor>
<md:KeyDescriptor use="encryption">
<ds:KeyInfo xmlns:ds="http://www.w3.org/2000/09/xmldsig#">
<ds:X509Data>
<ds:X509Certificate>MIIDAzCCAeugAwIBAgIJANkWspLTHos8MA0GCSqGSIb3DQEBBQUAMBgxFjAUBgNV
BAMMDXNwaWQubGVjY2UuaXQwHhcNMTcxMDA3MTU0MzUxWhcNMjcxMDA1MTU0MzUx
WjAYMRYwFAYDVQQDDA1zcGlkLmxlY2NlLml0MIIBIjANBgkqhkiG9w0BAQEFAAOC
AQ8AMIIBCgKCAQEAnyRZeRWZur9++fi33+OmvwCNVkDGwyzrAiqLesuypOrPUm9E
c2kgkOJgfoR4mq62pulh3PeEhSgaqdl/sxuKAhNObJMbAf8++Qj+LOVJxcgR6YvD
7WkMCueaQ9J5eKDJsHyEwGSLpufGD1zjcxAZTdaj5EvIyNN0zuPx6SNkb0ebhVza
ui8T6VoAxtSUFs65AkiH+UWUnJw7IRBlVfHqVFwJhHhM1mfafXSwCtiGz7I4lnX1
Wgp6owFOXQRirRZBe4rXsBwJr80ig4tTlAArcFnDAVA8sdWZobXaNv0xgZu4IvRN
+/GiiXF0r13TxY1saswdbdYHzBjEeluOvk2q3wIDAQABo1AwTjAdBgNVHQ4EFgQU
dyfs1wubmkpmsy4ozv5bG8b74mgwHwYDVR0jBBgwFoAUdyfs1wubmkpmsy4ozv5b
G8b74mgwDAYDVR0TBAUwAwEB/zANBgkqhkiG9w0BAQUFAAOCAQEAnZKa4B3j5Rgl
uVRa6ELL5PbPVzmq0rfLm0n76jiZ0AessvBiY4/HGmhkdRr2FdIm/Ra9wRsWQE0c
ho9ZjRV3ha5nocnSmkQ5THzNn+8UafDN+UavpZ8aY0qBUODDMk1pCL3a1Ly56rWE
lSOTog0O5tyCAEqEsB2LFyKOLGQBvXmwhtCOqXflrzB3yJuHhnHr5pMP0NX8yBtR
ayuf7j/2H4NAyirvangOc5x7ZcYA9IzTE+t/0cvHKHbmejsUq11yICnD9YSeqOoJ
0fgPN2O0BTGyqTmKm/0V0oTtOe3xDCDOyhYQY40b3PXI5ApEWvg2R/QqLY7RQ6Za
aGs3hPCw6A==</ds:X509Certificate>
</ds:X509Data>
</ds:KeyInfo>
</md:KeyDescriptor>
<md:SingleLogoutService
Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST"
Location="https://www.HIDDEN.it/logout" />
<md:NameIDFormat>urn:oasis:names:tc:SAML:2.0:nameid-format:transient</md:NameIDFormat>
<md:AssertionConsumerService
Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST"
Location="https://www.HIDDEN.it/sendresponse"
index="0"
isDefault="true" />
<md:AttributeConsumingService index="1">
<md:ServiceName xml:lang="it">test</md:ServiceName>
<md:ServiceDescription xml:lang="it">test</md:ServiceDescription>
<md:RequestedAttribute Name="spidCode" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:basic"/>
<md:RequestedAttribute Name="name" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:basic"/>
<md:RequestedAttribute Name="gender" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:basic"/>
<md:RequestedAttribute Name="fiscalNumber" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:basic"/>
<md:RequestedAttribute Name="familyName" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:basic"/>
<md:RequestedAttribute Name="dateOfBirth" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:basic"/>
<md:RequestedAttribute Name="email" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:basic"/>
</md:AttributeConsumingService>
</md:SPSSODescriptor>
</md:EntityDescriptor>
METADATA IDP SPID-TESTENV2:
<md:EntityDescriptor xmlns:md="urn:oasis:names:tc:SAML:2.0:metadata" entityID="http://www.HIDDEN.it:8088">
<md:IDPSSODescriptor protocolSupportEnumeration="urn:oasis:names:tc:SAML:2.0:protocol" WantAuthnRequestsSigned="true">
<md:KeyDescriptor use="signing">
<ds:KeyInfo xmlns:ds="http://www.w3.org/2000/09/xmldsig#">
<ds:X509Data>
<ds:X509Certificate>MIIC7TCCAdWgAwIBAgIJALkxwUJ2vJLaMA0GCSqGSIb3DQEBCwUAMA0xCzAJBgNV
BAYTAklUMB4XDTE5MDUwMjA3NTE0MloXDTE5MDYwMTA3NTE0MlowDTELMAkGA1UE
BhMCSVQwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQC+HH5/I50gHhS4
P7ajFW5199K/QMqjvWCZm91YzYuSxs7wCQxmMwUPvcwUyEpKD8iVAVLFbRs2g7/q
pujtRvD/c7I6S9PNglPIeDhwfQn3I1O6heivJ5UXDJdWBxZbbpIambMjPWF8wkz8
g6iQPGSj2TwEKS5futWo+E2nxXeFjDgJcOEDS3zqS/FKysS89C2JyPC2eGZAKXY/
nXDv0WGF3LGE6QE0MrFR5yh+B+dejXw3NGM7x8+hJvA0PyFbbR/mS2xu6xgaBozL
pjk4GXxfUaEm+2gxFxu9VO/9N4NMSInPCzS0X3bwLBzYx47WhAi2md1rUhAXlhxE
oljFDis7AgMBAAGjUDBOMB0GA1UdDgQWBBQg5wT9evUQD6jdfXuH8i3s8kZ4FDAf
BgNVHSMEGDAWgBQg5wT9evUQD6jdfXuH8i3s8kZ4FDAMBgNVHRMEBTADAQH/MA0G
CSqGSIb3DQEBCwUAA4IBAQC14CEREMccumZTmAS7hZsnYL/Q5JZ3dBAywb1KgQhQ
jY+TUaT9BhX90grXhGzdWhdljg4zMfh9QhOPHwgWgDE3EAlXnEH9jedaoihw9tCq
bEpHbgHCocnERD9ZWYwnB3tTf7DVhG/TSuVeQXSDyL0zOfG/+BRPUk1FJhIo7D7C
lMqvKn6Htmdxs6rN/6YI/5oXbtLH0deDHGGBhjw8Yn1V4SZSqijqfViX0FJNKSGA
WSpgBA7W6TrsBFPo7Eb497iVkGb2BPHJxuOzPxOUautJ182884rtoc0RhOq7F0cF
guAIyhDgfoZgp9q90PpF+x4I09UC5SzpnPlSyeWrx3R0
</ds:X509Certificate>
</ds:X509Data>
</ds:KeyInfo>
</md:KeyDescriptor>
<md:SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="http://www.HIDDEN.it:8088/slo"/>
<md:SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect" Location="http://www.HIDDEN.it:8088/slo"/>
<md:NameIDFormat>urn:oasis:names:tc:SAML:2.0:nameid-format:transient</md:NameIDFormat>
<md:SingleSignOnService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="http://www.HIDDEN.it:8088/sso"/>
<md:SingleSignOnService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect" Location="http://www.HIDDEN.it:8088/sso"/>
<saml:Attribute xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion" xmlns:xs="http://www.w3.org/2001/XMLSchema" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" Name="ivaCode"/>
<saml:Attribute xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion" xmlns:xs="http://www.w3.org/2001/XMLSchema" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" Name="fiscalNumber"/>
<saml:Attribute xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion" xmlns:xs="http://www.w3.org/2001/XMLSchema" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" Name="familyName"/>
<saml:Attribute xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion" xmlns:xs="http://www.w3.org/2001/XMLSchema" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" Name="registeredOffice"/>
<saml:Attribute xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion" xmlns:xs="http://www.w3.org/2001/XMLSchema" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" Name="dateOfBirth"/>
<saml:Attribute xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion" xmlns:xs="http://www.w3.org/2001/XMLSchema" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" Name="name"/>
<saml:Attribute xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion" xmlns:xs="http://www.w3.org/2001/XMLSchema" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" Name="idCard"/>
<saml:Attribute xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion" xmlns:xs="http://www.w3.org/2001/XMLSchema" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" Name="companyName"/>
<saml:Attribute xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion" xmlns:xs="http://www.w3.org/2001/XMLSchema" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" Name="spidCode"/>
<saml:Attribute xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion" xmlns:xs="http://www.w3.org/2001/XMLSchema" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" Name="placeOfBirth"/>
<saml:Attribute xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion" xmlns:xs="http://www.w3.org/2001/XMLSchema" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" Name="countyOfBirth"/>
<saml:Attribute xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion" xmlns:xs="http://www.w3.org/2001/XMLSchema" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" Name="gender"/>
<saml:Attribute xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion" xmlns:xs="http://www.w3.org/2001/XMLSchema" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" Name="mobilePhone"/>
<saml:Attribute xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion" xmlns:xs="http://www.w3.org/2001/XMLSchema" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" Name="expirationDate"/>
<saml:Attribute xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion" xmlns:xs="http://www.w3.org/2001/XMLSchema" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" Name="address"/>
<saml:Attribute xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion" xmlns:xs="http://www.w3.org/2001/XMLSchema" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" Name="digitalAddress"/>
<saml:Attribute xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion" xmlns:xs="http://www.w3.org/2001/XMLSchema" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" Name="email"/>
</md:IDPSSODescriptor>
</md:EntityDescriptor>
Quale potrebbe essere il problema?
Grazie